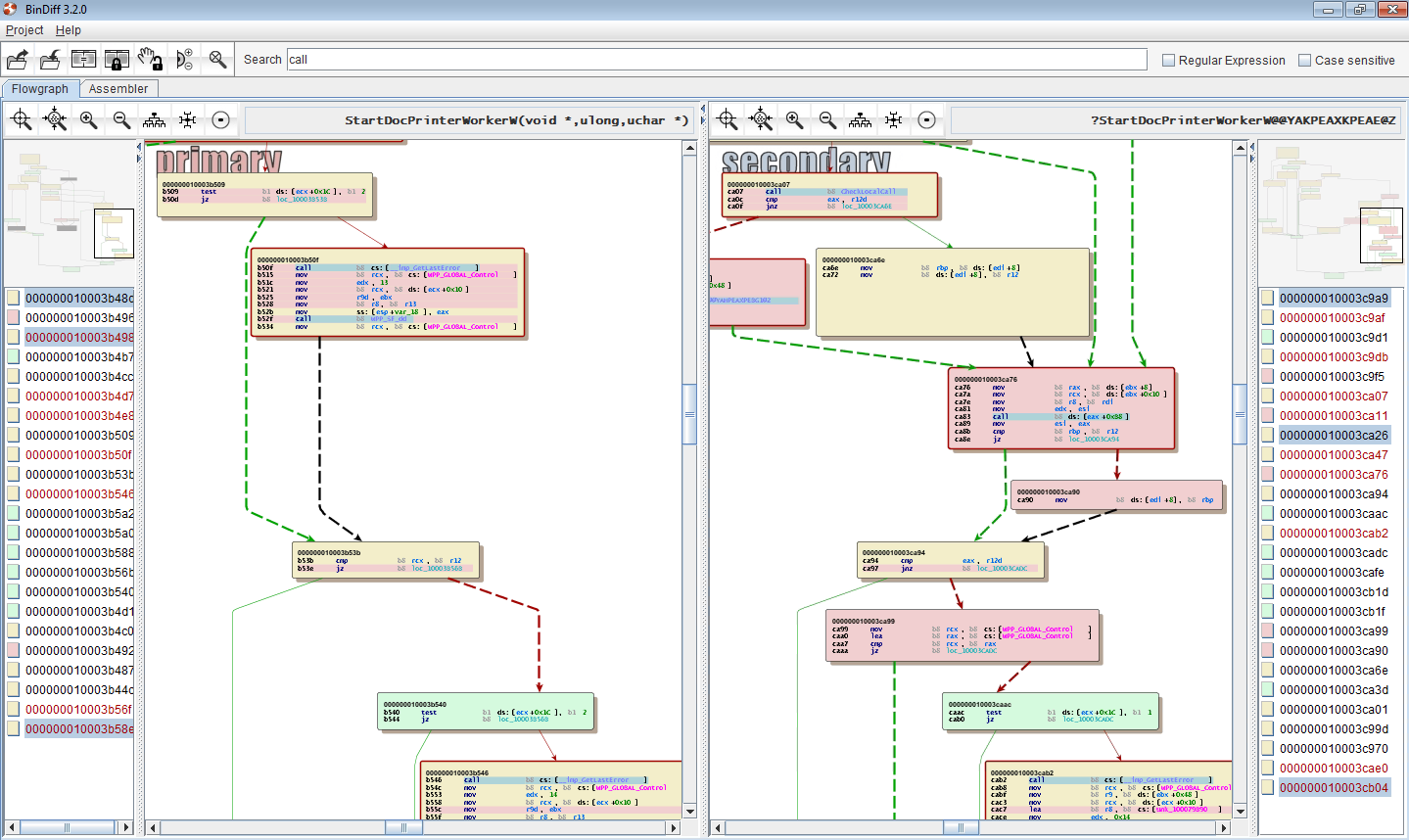
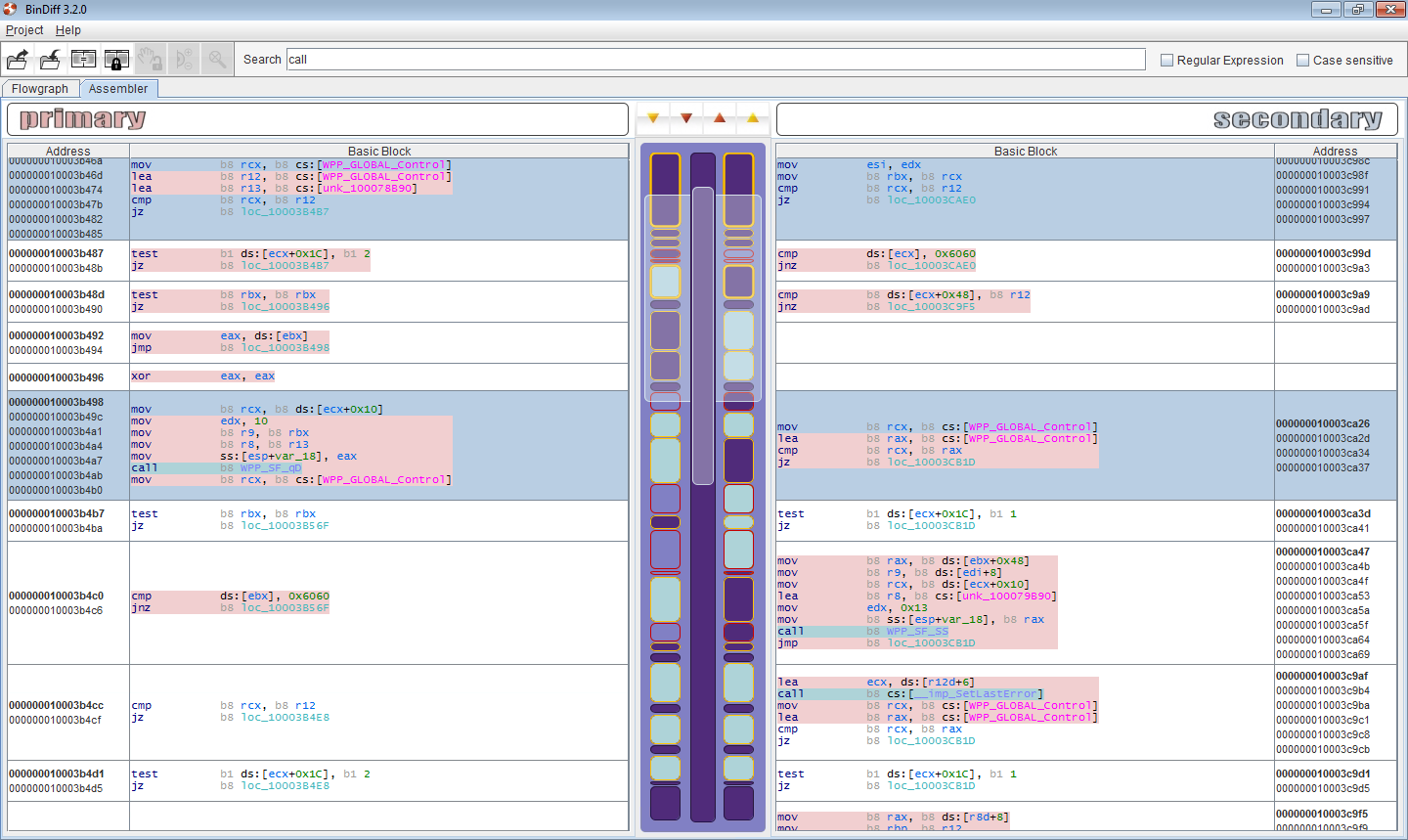
We are pleased to announce the official BinDiff 3.2.0 release. zynamics BinDiff is the leading comparison tool for binary files, that assists vulnerability researchers and reverse engineers all over the world to quickly find differences and similarities in disassembled code. BinDiff uses a unique graph-theoretical approach to compare executables by identifying identical and similar functions, which is resilient even against changes in binaries introduced by different compilers and optimization settings.
With BinDiff one can conveniently identify and isolate fixes for vulnerabilities in vendor-supplied patches. One can also port symbols and comments between disassemblies of multiple versions of the same binary or gather evidence for code theft or patent infringement. BinDiff 3.2.0 compares binary files for x86, MIPS, ARM, PowerPC, and any other CPU architectures supported by IDA Pro. BinDiff displays function matches between two binaries in a clear way and easily ports function names, anterior and posterior comment lines, standard comments and local names from one disassembly to another.
So, what are the new features in zynamics BinDiff 3.2.0? In a nutshell, besides many bug fixes and a better IDA integration, the quality of the diff engine has been improved. Also, this version is shipped with a new C++ based exporter plug-in for IDA which unifies the export process between BinNavi and BinDiff. For more information, refer to the previous blog post titled “BinDiff 3.2 public beta phase starts today“, or take a look at the complete change list, which can be found in the manual.
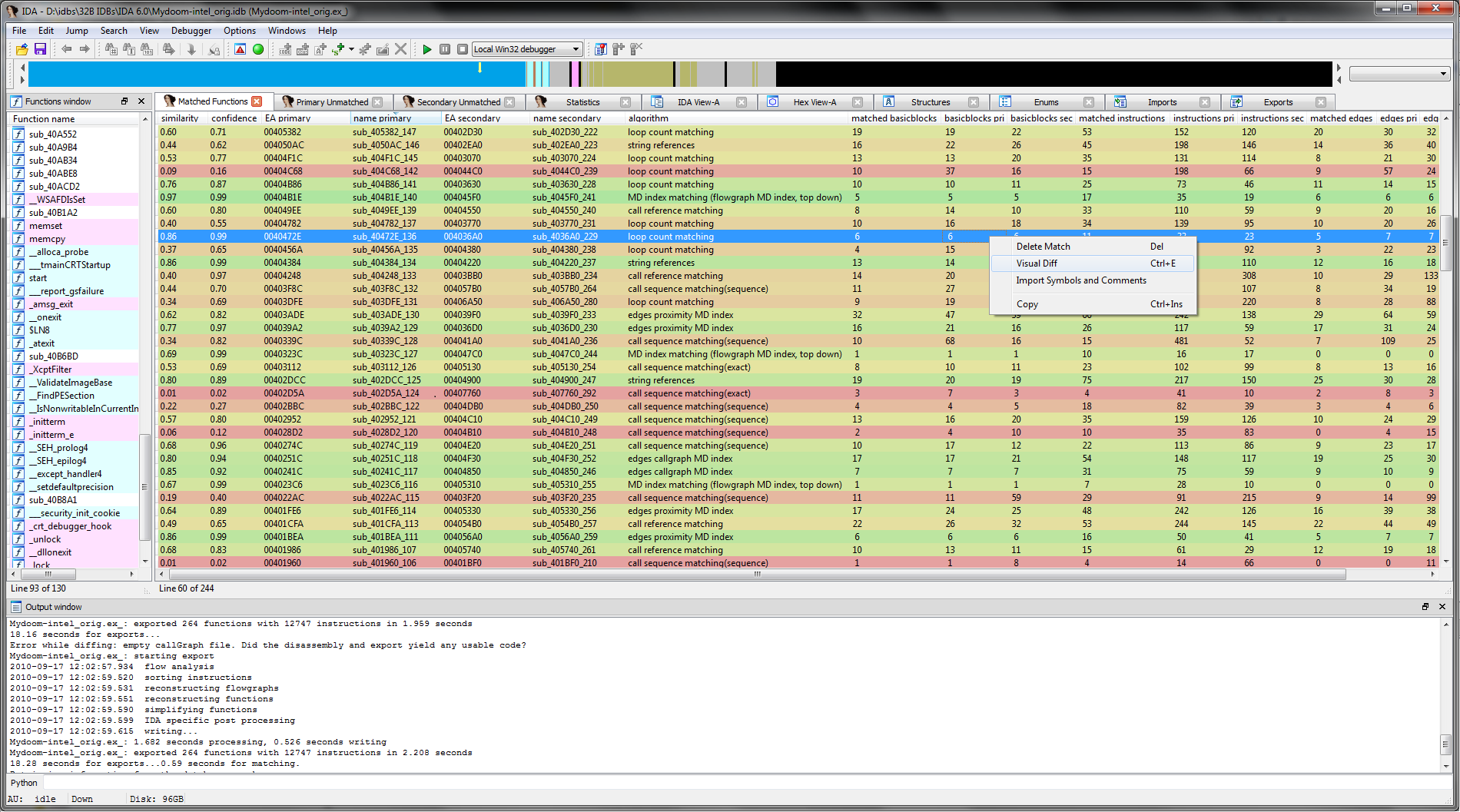
The previous image shows the new “Matched Functions” view with a diff of two MyDoom binaries that were build by different compilers and with different optimization settings. Each match is colored from green to red according to the respective similarity in both binaries.
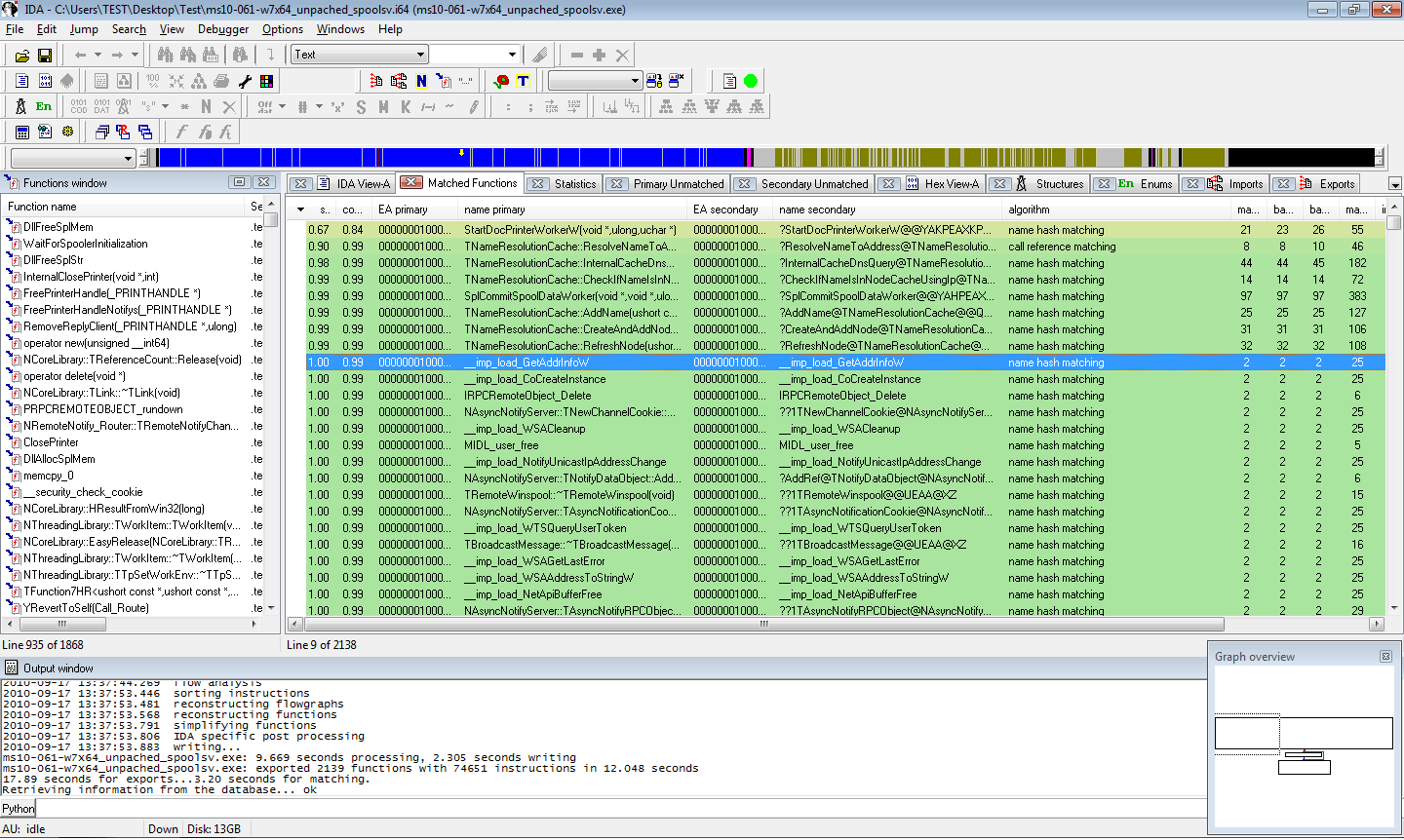
The image above shows the “Matched functions” view in IDA of a patch diff (MS-10-061 for Windows 7 x64). Changed functions can be easily spotted by sorting the table by similarity.
If you have any questions, please leave a comment or contact the zynamics support. If you are interested in a trial version, please write an email to info@zynamics.com. More screenshots and an order form can be found here.