Today I analyzed a malicious PDF file that contained more than 1100 lines of heavily obfuscated malicious JavaScript code. To make it easier for me to deobfuscate the code, I added two new features to our PDF malware analysis tool PDF Dissector: Variable references and snapshot histories.
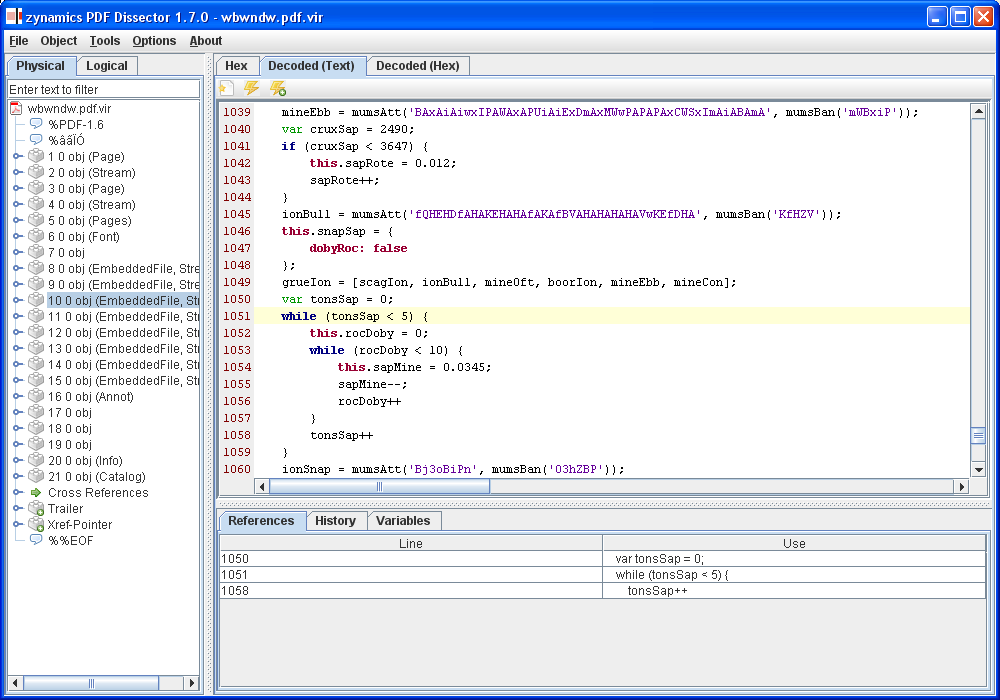
The variable references feature shows you where variables are used in JavaScript code. Just place the caret over a variable identifier and all lines that use that variable are shown to you. You can see what this feature looks like in the screenshot below.
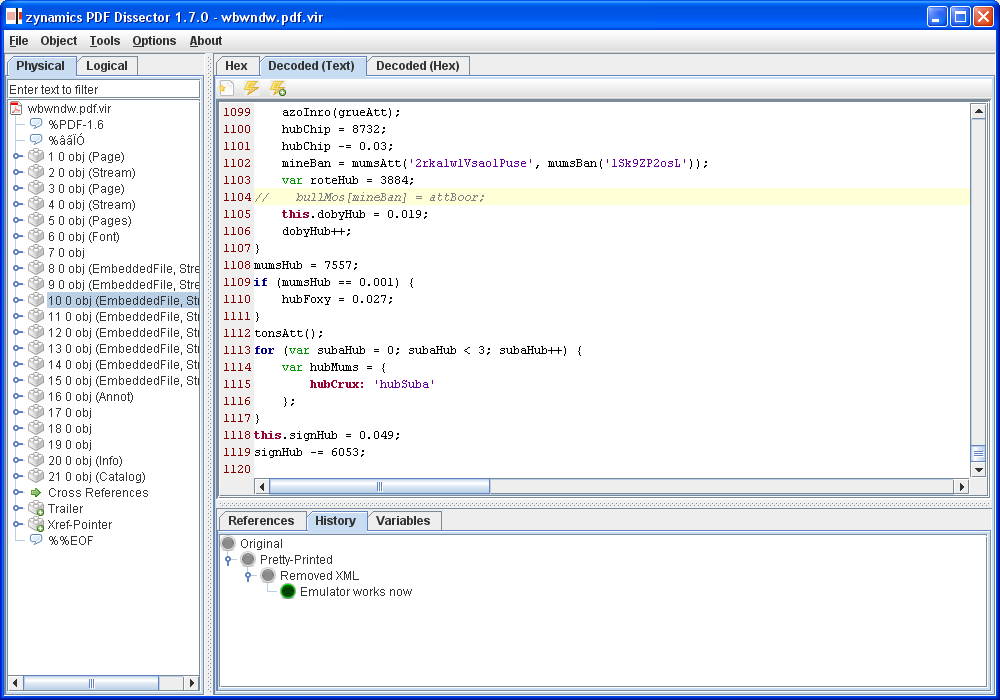
The snapshot history feature allows you to take JavaScript source snapshots of known states. Later on, you can then revert to the source code to the recorded snapshots. This is very useful when you accidentally remove JavaScript code that later turns out to be needed after all. The screenshot below shows you a snapshot tree of four named snapshots I made during different states of the deobfuscation process.
To learn more about PDF Dissector, please visit the product site or the PDF Dissector manual.
How much costs this software ? And How can I eventually buy it ?
Is it possible to purchase PDF Analyzer? How much does it cost?
Since the time the zynamics developer team joined Google I never found an info where to buy this application. I guess there is a real market for PDF dissector, especially since PDF malware becomes more popular again recently.