Hi everyone,
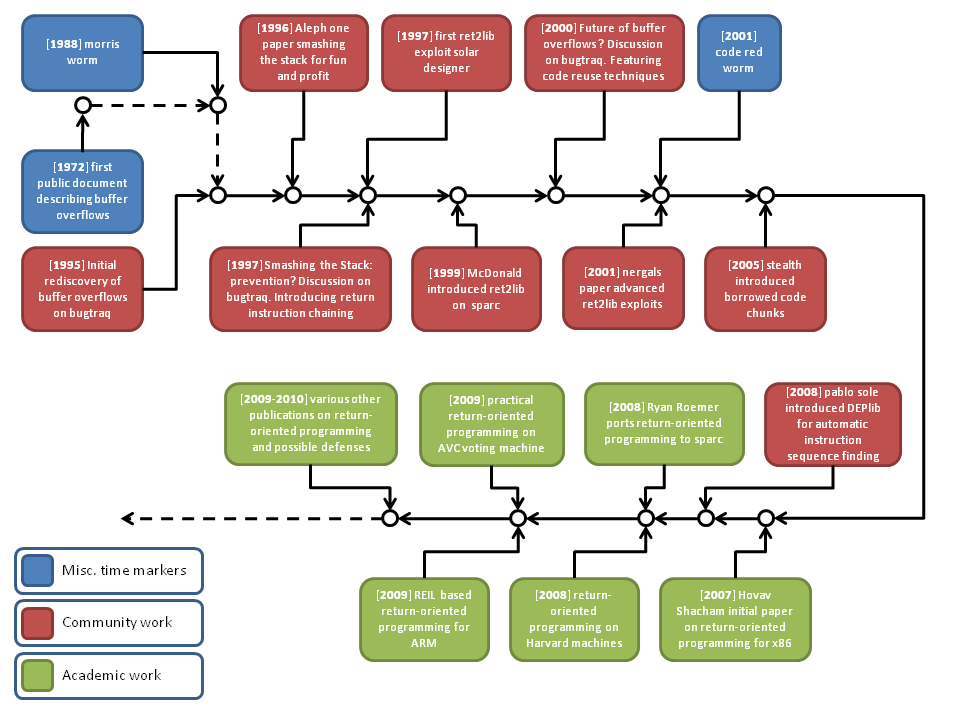
today at CanSecWest Thomas and I gave a talk where we announced the BinCrowd community server which zynamics makes available to the reverse engineering community for free. BinCrowd is a collaborative reverse engineering tool that can be used by reverse engineers to keep a repository of reverse engineered information and share this information with friends and colleagues.
The core technology behind BinCrowd is basically a huge database of function information which can be accessed using BinDiff-style algorithms. This allows you to efficiently store information about disassembled functions in a database and to use that database to compare functions from different binary files.
Imagine you are a reverse engineer hunting for new vulnerabilities. Here is what BinCrowd can do for you:
- You can use BinCrowd to look up whether anybody else in the BinCrowd community has analyzed a particular file before. If the file is already in the database, you can download reverse engineering information like function descriptions or argument names from the database. Due to the fuzzy matching algorithms behind BinCrowd even different versions of the target file are considered.
- BinCrowd tells you what static libraries are used by the file. If BinCrowd determines that your file is linked against an open-source library you can start reading the original source code instead of the disassembled code.
- BinCrowd tells you what version of a library is used. If BinCrowd tells you that a vulnerable version of zlib is used in your file, you can go down that path during your audit.
- You can reverse the lookup process too. If you have a vulnerable function you can ask BinCrowd in what other files this function is used. This will potentially give you many more vulnerable programs without any effort.
Or maybe you are a malware analysis specialist. Your workflow probably differs from that of a vulnerability researcher. Nevertheless, BinCrowd is very useful for you too.
- You can use BinCrowd as a repository of malware information. If you have identified and documented a certain rootkit hiding technology you can import information from your earlier analysis to new pieces of malware that use the same code.
- You can use BinCrowd to share information with colleagues from your malware analysis team and even with people from outside your team.
- If you are working on a team where information flow is restricted by clearance levels you can use BinCrowd as a central information repository. BinCrowd access roles will take care that people with a lower clearance can not download information entered into the system by people with a higher clearance.
There are potentially many more uses for BinCrowd since we are only at the beginning of a long road of creating a repository for reverse engineered information. If you are interested on joining us on that road you can sign up to the community server for free at http://bincrowd.zynamics.com.
To use BinCrowd you only need
- IDA Pro 5.6
- IDAPython 1.3.2
- The IDA Pro BinCrowd plugin which you can get from http://github.com/zynamics/bincrowd-plugin-ida
- An account on the BinCrowd community server
Happy shaREing and caring!
Finally, here are the slides Thomas and I used for our talk.
[slideshare id=3856188&doc=shareingiscaring-100325164546-phpapp01-100426045802-phpapp01]