Peter Silberman and I will be presenting, this Wednesday at BlackHat Europe 2010, our latest peek into the malware world.
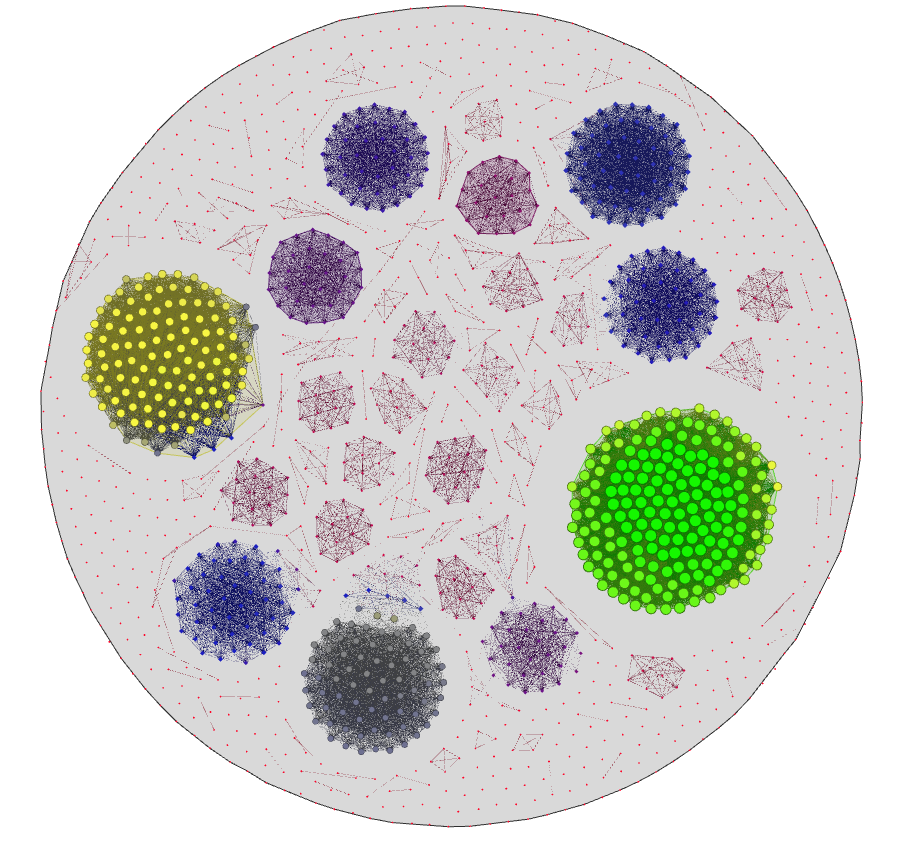
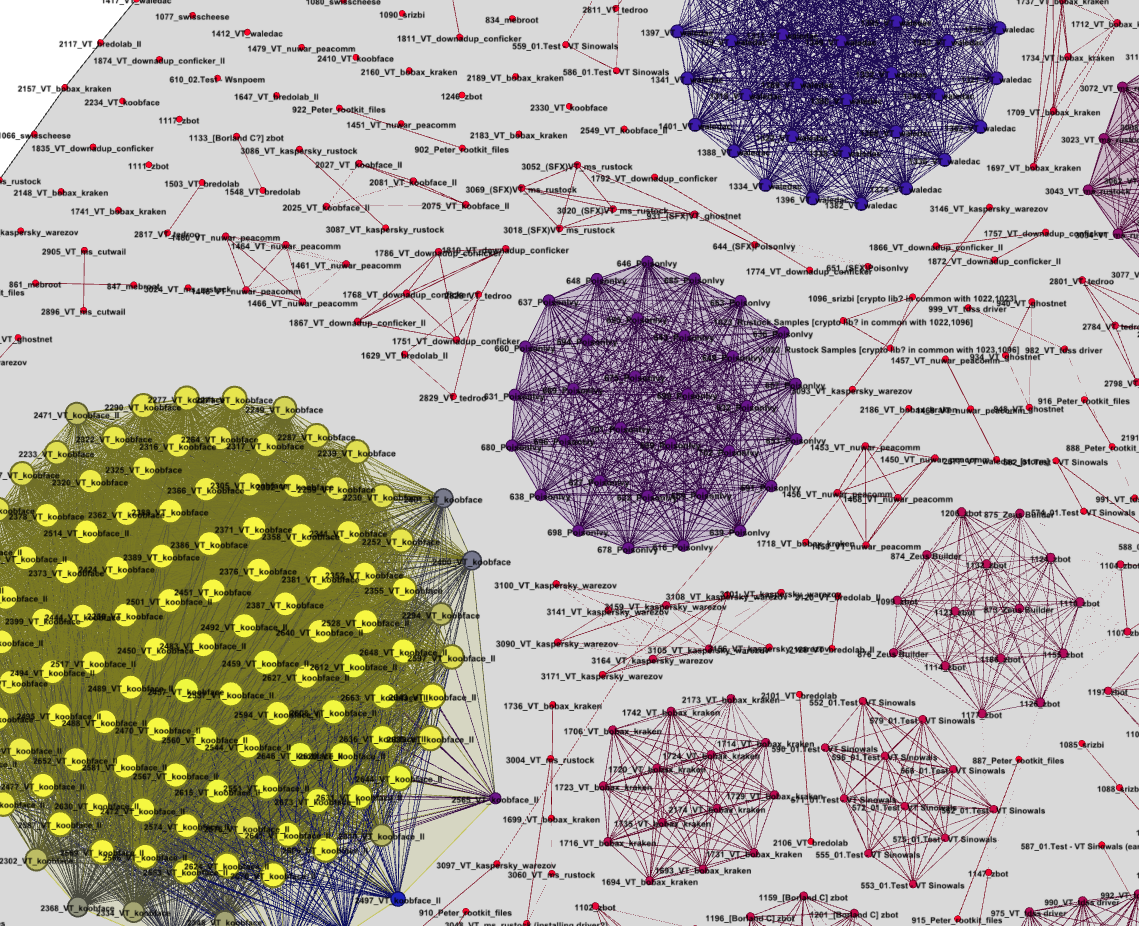
In this talk we follow up from our previous “State of Malware: Explosion of the Axis of Evil” , where we explored some of the idiosyncrasies of mass-malware vs. the ones in targeted malware. This time around we decided to try to spot actual code-sharing among a reasonably diverse corpus of recent malware obtained from VirusTotal.
Using some of the technology we’ve developed in zynamics to automatically classify malware we attempted to find relations between malware samples that would indicate that code had been shared, possibly indicating collaborative efforts of malware developers or even giving clues about common authorship.
If you want to hear what it is that we found out, don’t hesitate in dropping by our talk Wednesday 16:45h
See you there!
[…] with the line up of this SANS EU conference. It has a very eclectic mix of people talking. Ero Carrera will be dicussing malware analysis. While Ero isn’t a forenscitar, his insight into malware […]
[…] with the line up of this SANS EU conference. It has a very eclectic mix of people talking. Ero Carrera will be dicussing malware analysis. While Ero isn’t a forenscitar, his insight into malware […]