I have previously blogged about VxClass and our algorithms for automated generation of byte signatures here and here and here. I have also blogged about private signatures beforehand, a concept that I think has great relevance for defense against (and response to) targeted attacks. One point I left open in the previous blog post was the following question:
How do I actually use the byte signatures in a real-world scenario?
In this post, I will answer that question: We will use the latest version of Mandiant’s Memoryze and VxClass and walk through the entire process of memory acquisition, malware classification, signature generation and signature deployment. In detail, our steps are going to be the following:
- We will pre-populate a VxClass system with a good quantity of Zeus samples
- We will examine the clusters generated from this
- We infect a previously clean XP with a new Zeus sample
- We identify the suspicious memory sections that were created by Zeus using Memoryze and AuditViewer, two great (and free!) tools that Mandiant has released
- We acquire the injected memory sections from the infected system and submit them to VxClass
- VxClass recognizes the similarity to previously submitted Zeus samples and generates a byte signature to detect the entire cluster of both old and new Zeus variants. This signature is unique to us, and can be used to detect infections by this malware on any Windows machine.
- The signature is then fed into Memoryze to identify the infection on other machines
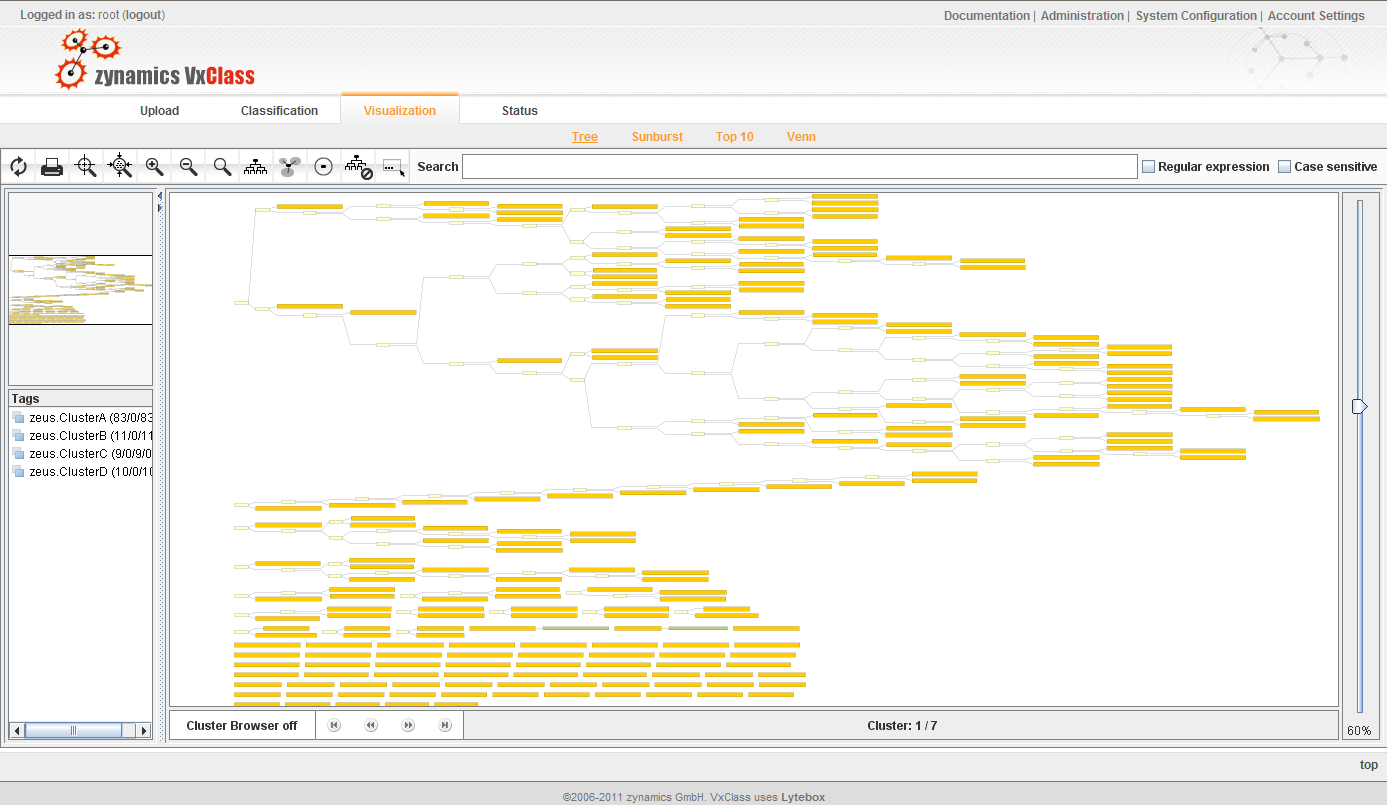
Wow, that’s quite a list. So where do we start? We start out by examining a small set of about 180 malware samples that we pre-populated a fresh VxClass with. These samples were labeled “Zeus” or “Zbot” by some anti-virus software, so we assume they are Zeus variants.VxClass has generated family trees, and assigned most of the files to these trees.
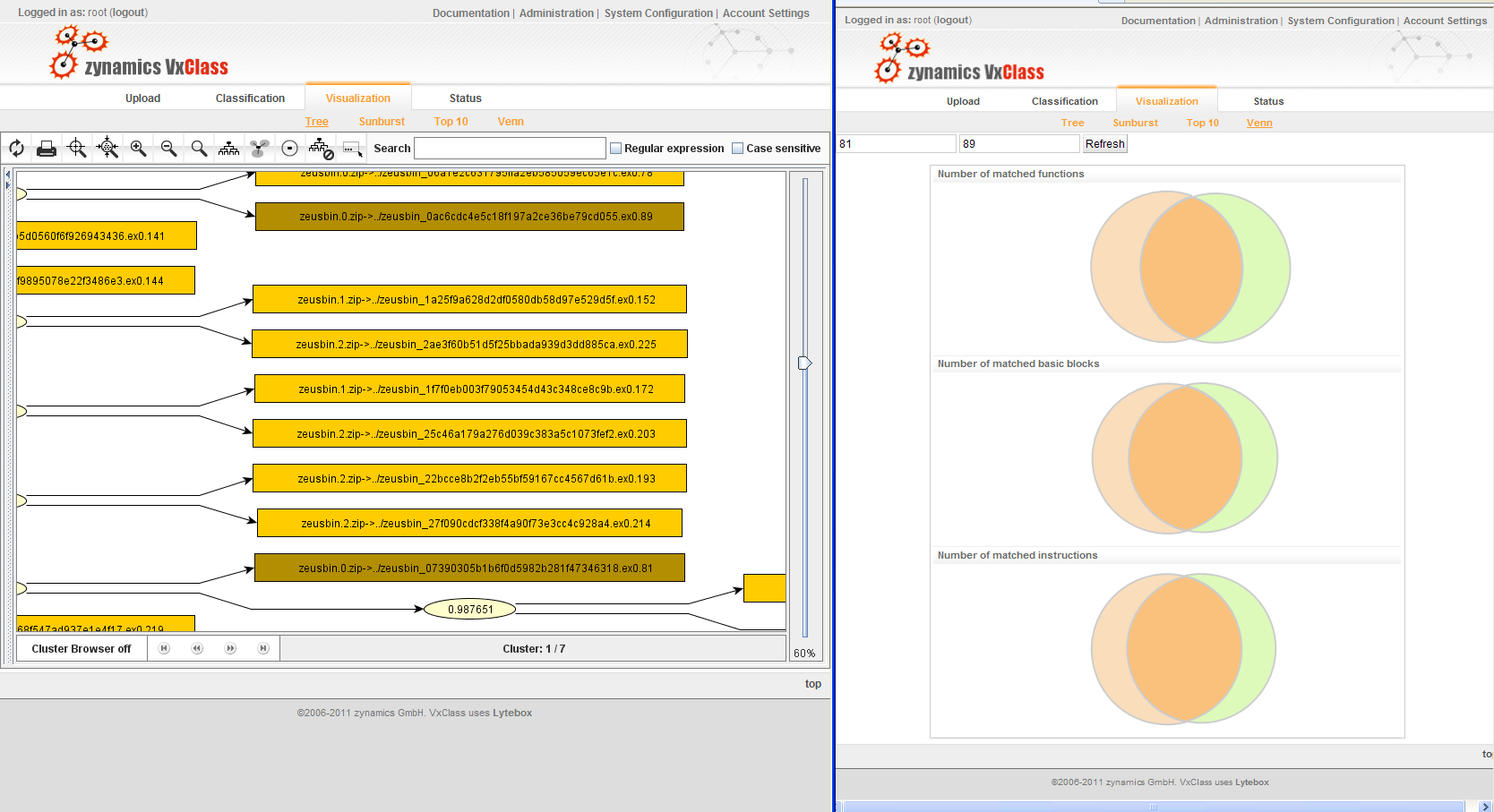
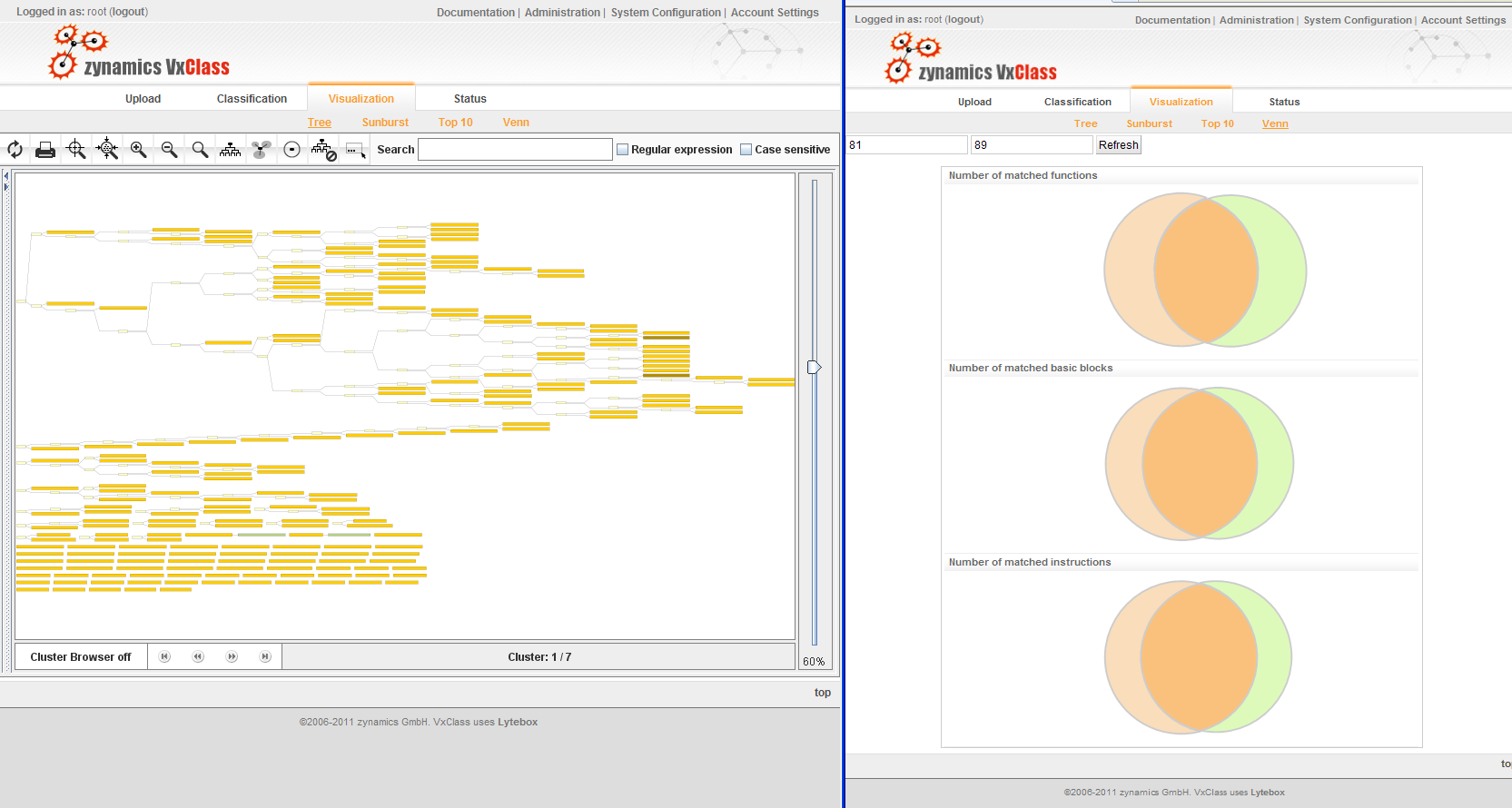
In the next two pictures, it will become evident what the “similarity score” between two samples means: It indicates how much overlap there is between the code of the two executables under consideration. To further illustrate the issue, we drew some Venn diagrams illustrating the overlap between the highlighted samples on the right hand side.
The next screenshot shows where in the family tree these two items are located (you might have to load the non-thumbnail version to actually see this):
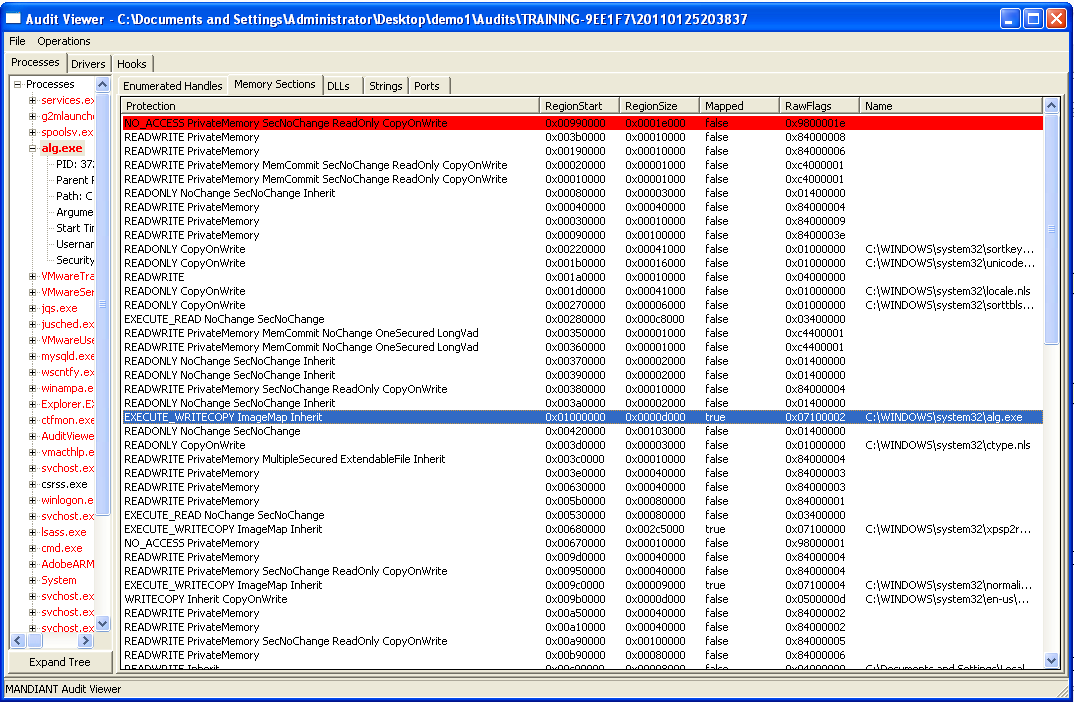
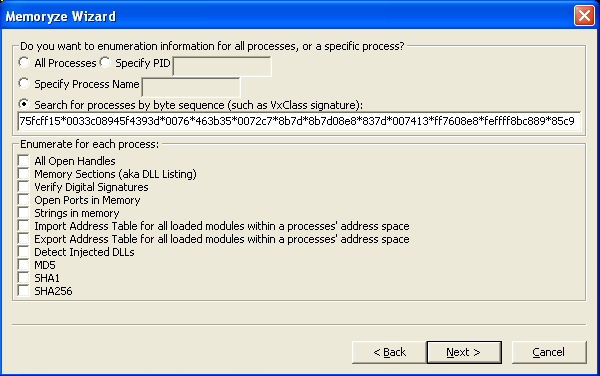
But enough of this. As a next step, I infect a vanilla XP machine with a new random sample that was labelled Zeus — one that VxClass has never seen before. After having done this, I use Memoryze (and AuditViewer, a nice GUI for it) to identify the memory sections that have been injected into various processes. To do this, you have to click through a few dialogs that ask you to configure the following things:
- The location of Memoryze
- The output path for the data
- Whether you wish to work from live memory (yes)
In the first step, we just want to identify those processes that Zeus injected itself into – we will acquire the injected memory separately. We hence check “Process Enumeration” and leave the “Acquisition” fields unchecked. Finally, we enable “Memory Sections” and “Detect Injected DLLs” to be enumerated for each process. AuditViewer now launches Memoryze, and after a brief waiting period we can inspect the results. AuditViewer is nice enough to highlight the processes that contain suspicious injected DLLs in red. Furthermore, we can immediately spot the problematic section of memory, because AuditViewer has highlighted it, too.
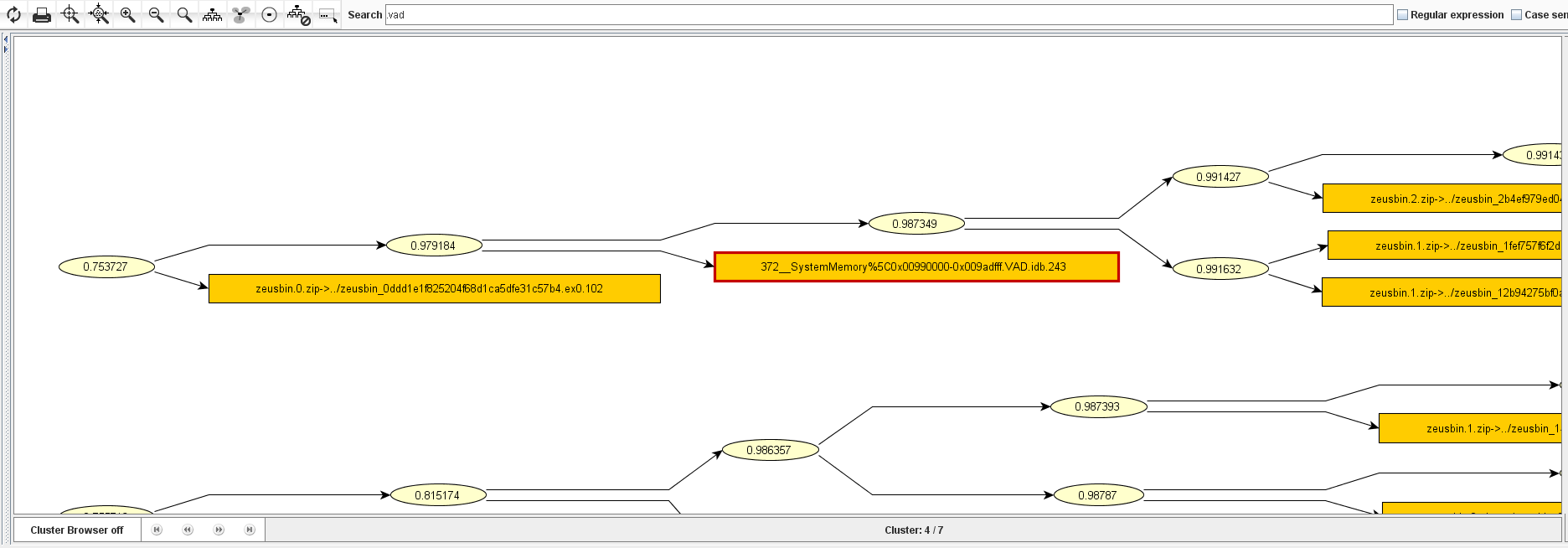
In the next step, we simply upload the .VAD file of this memory section to our VxClass box and look whether this is in any way similar to the code already in the box. And no surprise: It is quite similar to a number of other executables in the database:
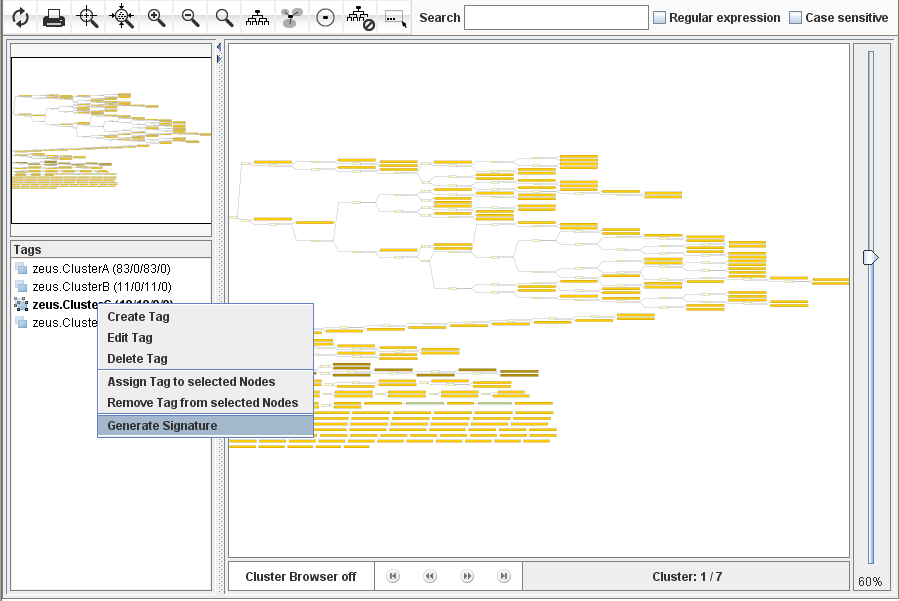
In the next step, we will want to generate a traditional byte signature for all executables in the relevant cluster. This is pretty easy — highlight them, assign a tag to them, and then right-click “create signature” (screenshot below).
A few seconds later, the signature is ready and can be downloaded (in ClamAV format) from the “Signatures” tab in the VxClass web UI. The generated signature is the following:
cluster.C.worm:0:*:81ec*000000*8b75*ff75* 56ff15*0033*8945*0f84*558bec83ec10565733f668* 0033ff8975fcff15*0033c08945f4393d*0076*463b35* 0072c7*8b7d*8b7d08e8*837d*007413*ff7608e8* feffff8bc889*85c9*3c20740b*013845fe7444* c645fe00e9e1000000*558bec81ec*020000*535633* 0000*0033*8d85*fdffff*5089*ff15*8d85*b301* 83f907750d*0085c075*6a07585068*8b7d188d043b8d440014* 8bf08975*020000*8365*00566a0033c0c645ff00e8* 06000085c00f85*010000*0fb645fd0fb70cc5*008b3d
This is clearly much longer than what would be strictly required – we usually generate much longer signatures than the bare minimum in order to minimize the risk of false positives. The cool thing about the signature is that it is private — e.g. no other user of VxClass would get the same signature (to be precise: the probability of another user getting the same signature is astronomically small). This means that unless you share this signature (like I did above), it remains as a “secret weapon” in your arsenal: The malware authors do not know what signature you are going to detect them with, so they can’t intentionally “break” this signature.
Now, an important question remains unanswered:
How does one deploy such a signature?
We have two options: We can use AuditViewer to configure Memoryze again, or we can simply run Memoryze from the command line with the appropriate configuration file to scan through the physical memory of a machine. In order to use AuditViewer, simply configure it as usual: Provide it with the location of Memoryze and tell it to analyze live memory. After you have done so, you mark the “enumerate processes” checkbox, and finally, you tell AuditViewer about the byte pattern you wish to search for:
AuditViewer will then launch Memoryze in the background which will scan through all processes and identify those that contain the pattern in question.
AuditViewer saves the current configuration for Memoryze in a file called out.xml in your Memoryze directory. This means you can simply make a copy of out.xml in your Memoryze directory and re-use it on other machines without having to re-run AuditViewer. Simply install Memoryze on a machine and then launch “Memoryze -script out.xml -o <outputdir>“.
You now have a new way of detecting variants of the malware that was used to attack you. But best of all: This method is secret – the signature isn’t shared with the wider world – and the attacker therefore has a much harder time immunizing his attack tools prior to the next attack.
To summarize: Combining VxClass with Memoryze and AuditViewer makes the acquisition and correlation of malicious code easy – but best of all, these tools also provide a quick and convenient way to automatically generate high-quality detection mechanisms that are kept secret from the attackers.
[…] This post was mentioned on Twitter by Matthieu Suiche, halvarflake, `Ivan, petersilberman, Mandiant and others. Mandiant said: RT @halvarflake: Using VxClass + Memoryze + AuditViewer to generate new private signatures for Zeus and scan for them: http://bit.ly/dOU58r […]
[…] a time with Memoryze and Audit Viewer. Thomas has a great write-up of how this process works here. I will not attempt to explain the article, but below is a glimpse. Two pieces of malware […]
[…] And of course this release also includes the signature generation component Thomas blogged about here, here and here. […]
[…] a time with Memoryze and Audit Viewer. Thomas has a great write-up of how this process works here. I will not attempt to explain the article, but below is a glimpse. Two pieces of malware […]