The 1.3.0 release of our PDF malware analysis tool PDF Dissector is primarily a bugfix release to undo some of the bugs introduced in 1.2.0. However, I have also added a cool new feature.
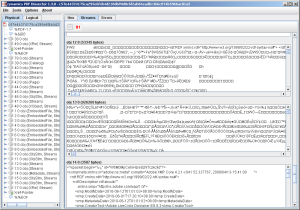
I have added a way to quickly browse through the content of all decoded data streams. This is very useful if you want to quickly see what data streams contain potentially malicious content like embedded Flash files or AcroForms code. To account for binary resources and text resources you can switch between text mode and hexadecimal mode.
The screenshow below shows what the new feature looks like. You can clearly see the embedded Flash file on object 12 (note the Flash file header starting with FWS).
To learn more about PDF Dissector please check out the manual.
[…] camoufler une attaque par pdf et comment la détecter : PDF Dissector par Sebastian Porst de Zynamics.com. A conserver pour gagner quelques secondes durant un CTF ? […]