We have all been taught (and intuitively felt) that traditional antivirus signatures are, for the most part, a waste of time. I think I have myself argued something similar repeatedly. One could say that “byte signatures don’t work” is accepted conventional wisdom in the security industry. Especially in the light of the recent (and much-publicized) Aurora-attacks, this conventional wisdom appears to ring truer than ever.
One thing though that I have personally always liked about the security industry was the positive attitude towards challenging conventional wisdom — re-examining the assumptions underlying this wisdom. In this post (and the upcoming sequel), I will do just that: I will examine the reasons why everyone is convinced that traditional byte signatures do not work and ask questions about the assumptions that lead us to this conclusion.
So. Why do we think that traditional antivirus signatures are a waste of time ?
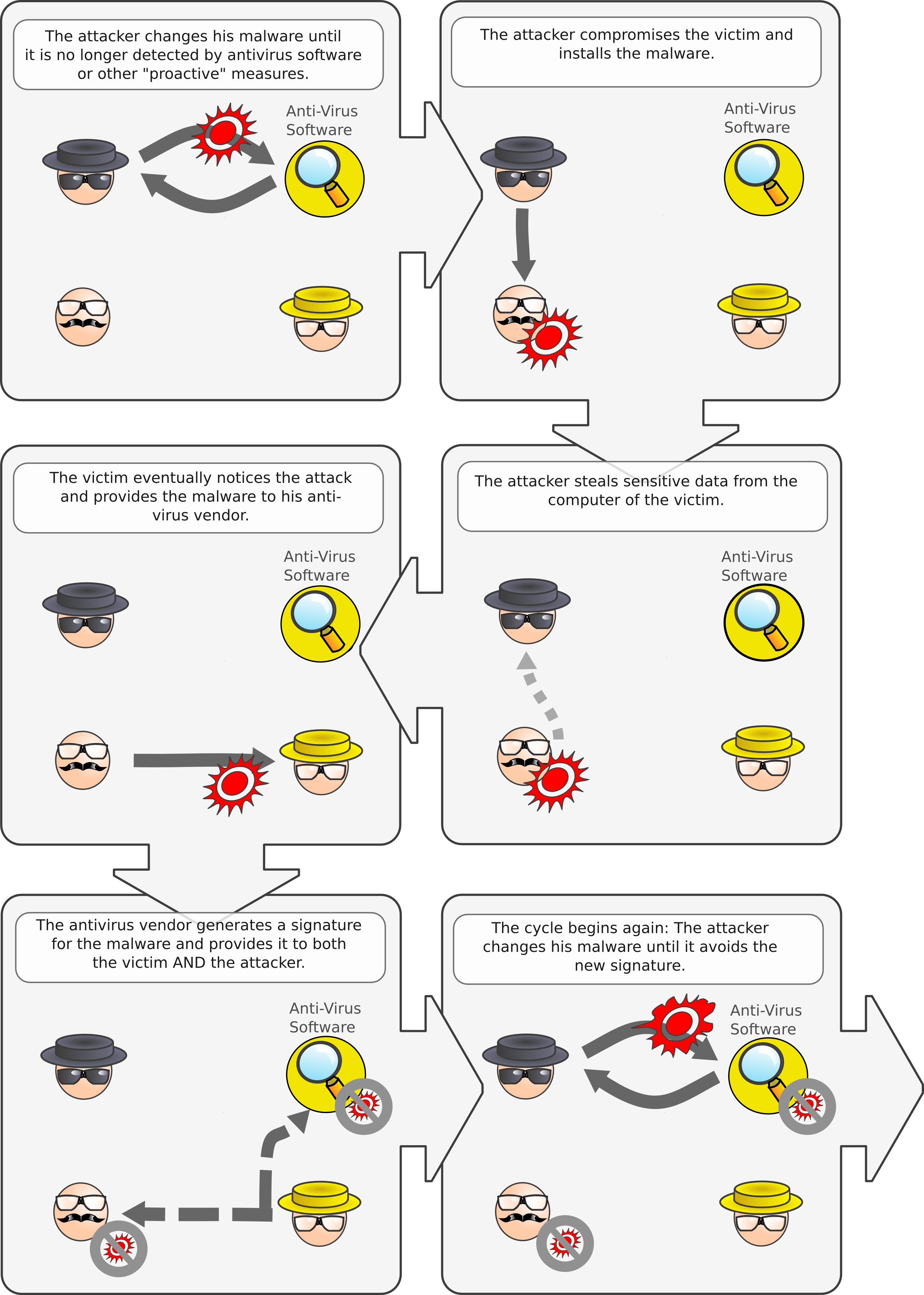
Let’s first recapitulate what the usual cycle in a targeted attack consists of:
- The attacker writes or obtains a backdoor component
- The attacker writes or obtains an exploit
- The attacker tests both exploit and backdoor against available AV tools, making sure that both are not detected
- The attacker compromises the victim and starts exfiltrating data
- The defender notices the attack, passes the backdoor to the AV company, and cleans up his network
- The AV company generates a signature and provides it to both the attacker and defender
- Goto (2)
This entire cycle can be clarified with a few pictures:
Let’s look at this diagram again. What properties of “byte signatures” does the attacker exploit in immunizing his software ? Well … none, really, except the fact that he fully knows about them before launching his attack. There is no information asymmetry: The attacker has almost the exact same information that the defender has. Through this, he is provided with a virtually limitless number of trial runs of his attack, and he can adapt his attack arbitrarily, over long time periods, until he is reasonably certain that it will be both successful and undetected.
The implication of this is that the underlying problem is not a feature of byte signatures, but rather a generic problem inherent in all security systems that provide identical data to both attackers and defenders and that have no information asymmetry at all.
In the next post, I will examine two approaches how this problem could be addressed to give the defender an advantage.
It’s the same thing with watermarking. If you make the detector public, the attacker can mutate the video by small amounts until it passes. You have to move to schemes such as forensic marking, where the detector is secret, in order to have asymmetry.
Nate, I suspect their next post will be a non-byte signature system derived from concepts Zynamics is quite familiar with – basic blocks signatures. Bindiff matches functions based on innate characteristics such as calls, variables, etc that are then examined as directed graphs. It seems logical given VxClass and Bindiff to extend that pattern matching to generic malware patterns ie “signatures”. Because unpacked malware isn’t going to fundamentally change often the (suspected soon to be proposed) system might employ a new class of signatures to detect malware variants based on sufficient correlation of known malicious graphs of malicious functions seen in malware.
Thereby it’s nearly impossible to avoid detection on unpacked malware assuming they’ve built the said system and malicious functions are sufficiently unique to avoid collisions with common non-malicious code.
I’m very interested in the engineering details as unpacking isn’t always trivial, the binary reversing is an expensive operation, and I believe the graph algorithms are likely NP-Hard. I’ve been interested in these strategies for a while so this is fairly exciting.
If I’m flatly wrong, that’s good too as it leaves me more fun stuff to develop. 🙂
[…] conventional wisdom on AV signatures (Part 2 of 2) By Thomas Dullien A while ago I posted a blog entry called “challenging conventional wisdom on AV signatures (Part 1 of 2)”. There, I […]
[…] previously blogged about VxClass and our algorithms for automated generation of byte signatures here and here and here. I have also blogged about private signatures beforehand, a concept that I […]
[…] of course this release also includes the signature generation component Thomas blogged about here, here and […]